React CSR vs SSR — Which One Should You Use?
· 7 min read
Hello everyone! In today's blog, we'll explore how to invite an AWS management account that is already part of another organization into a new organization. This process can be a bit tricky, but we'll walk you through it step by step. Let's get started!
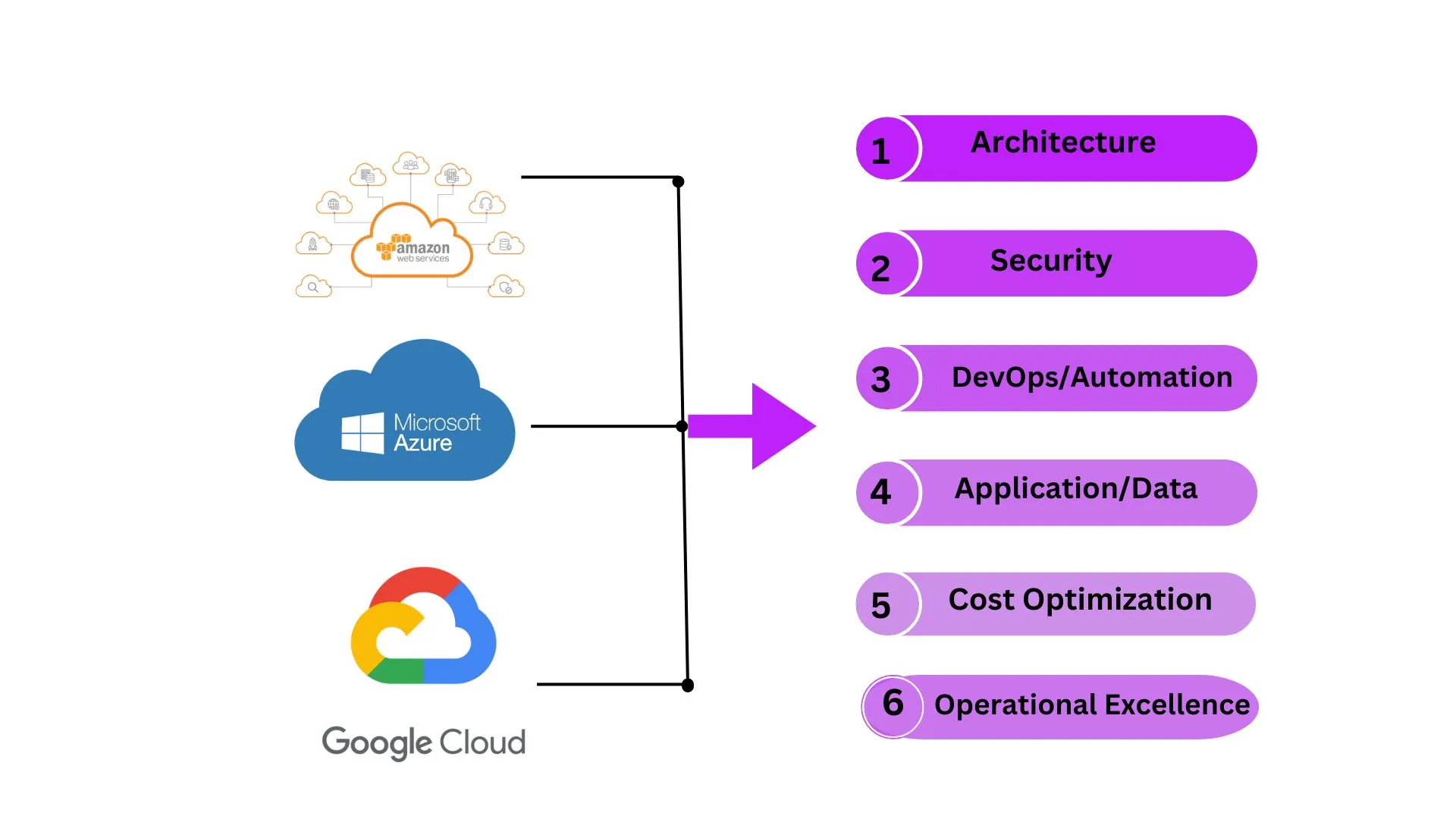
To become a good cloud architect it's important to understand the essential pillars that support a well-architected framework. This framework helps in designing, deploying, and maintaining cloud applications efficiently. Here are some of the key pillars and insights from our experience at Arena Technologies.