Your Data, Your Keys, Your Control: Bring your own keys to AWS CloudHSM - Part 1
Amazon Web Services (AWS) CloudHSM offers a robust solution for securing cryptographic keys and operations within the cloud, leveraging hardware security modules (HSMs) to enhance security. This guide walks through the process of setting up an AWS CloudHSM environment, from configuring EC2 instances to initializing and managing the HSM cluster.
Initial Setup: EC2 and CloudHSM Cluster
EC2 Configuration
- Instance Selection: Start by provisioning an Amazon EC2 instance, choosing either a
t2.microort2.smallwith Amazon Linux 2. - VPC Configuration: Ensure that the EC2 instance is set up within the same Virtual Private Cloud (VPC) as the intended CloudHSM cluster to facilitate seamless connectivity.
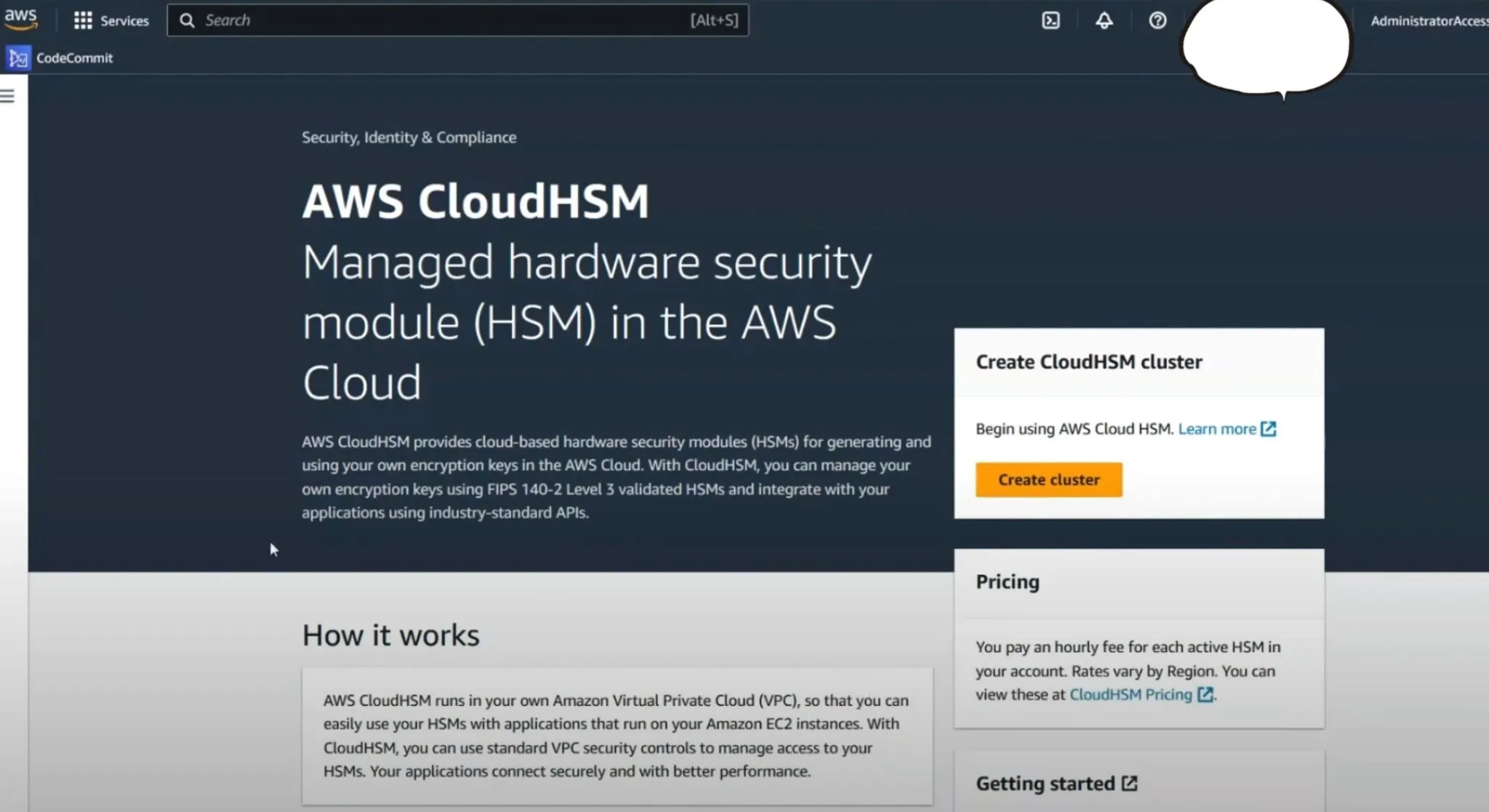
CloudHSM Cluster Creation
- Access AWS Console: Navigate to the CloudHSM section within the AWS Console and start the process by selecting "Create Cluster".
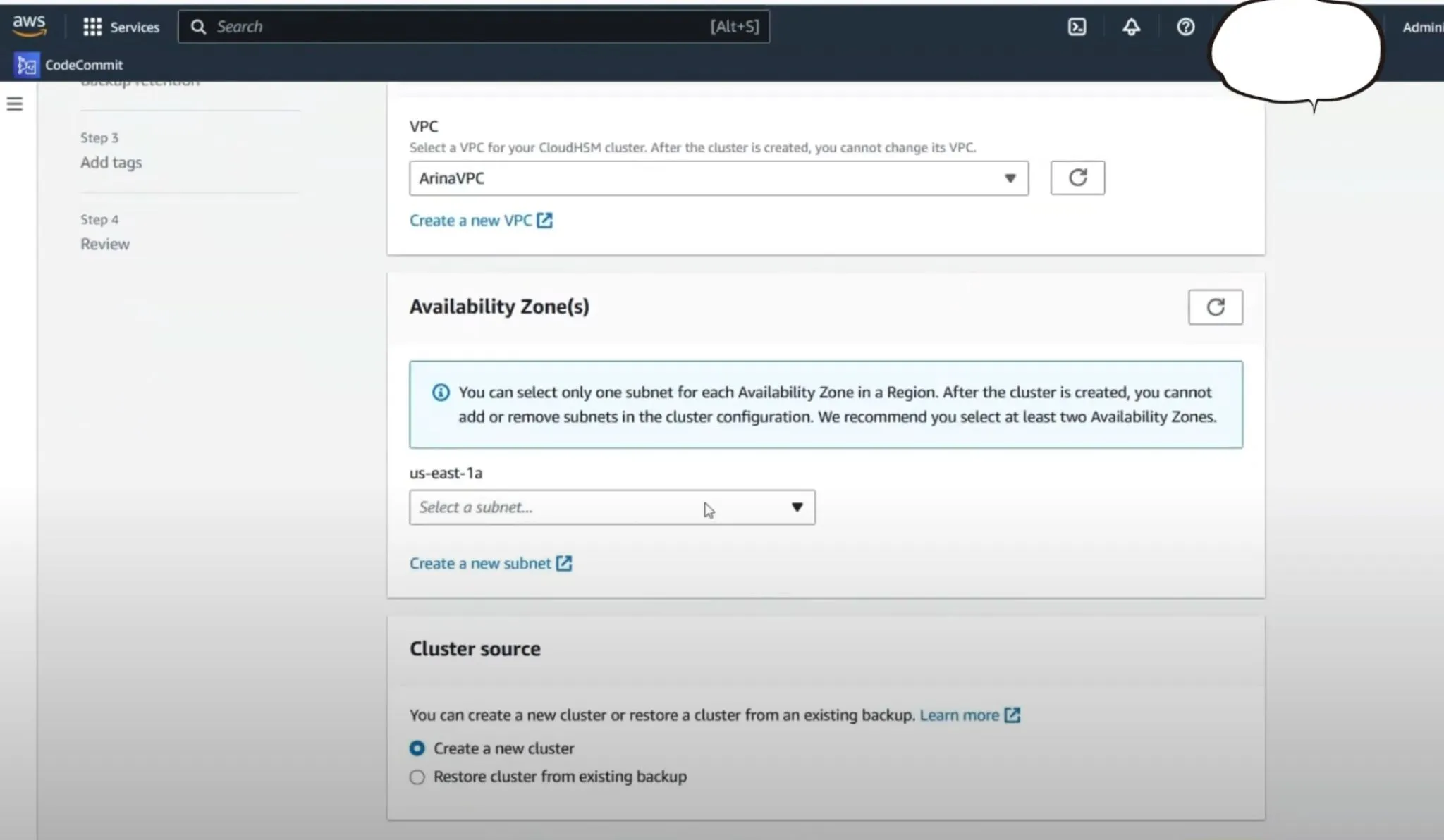
- VPC and AZ Selection: Choose the appropriate VPC and for simplicity in this setup, select only one Availability Zone (AZ), though typically two is recommended for better resilience.
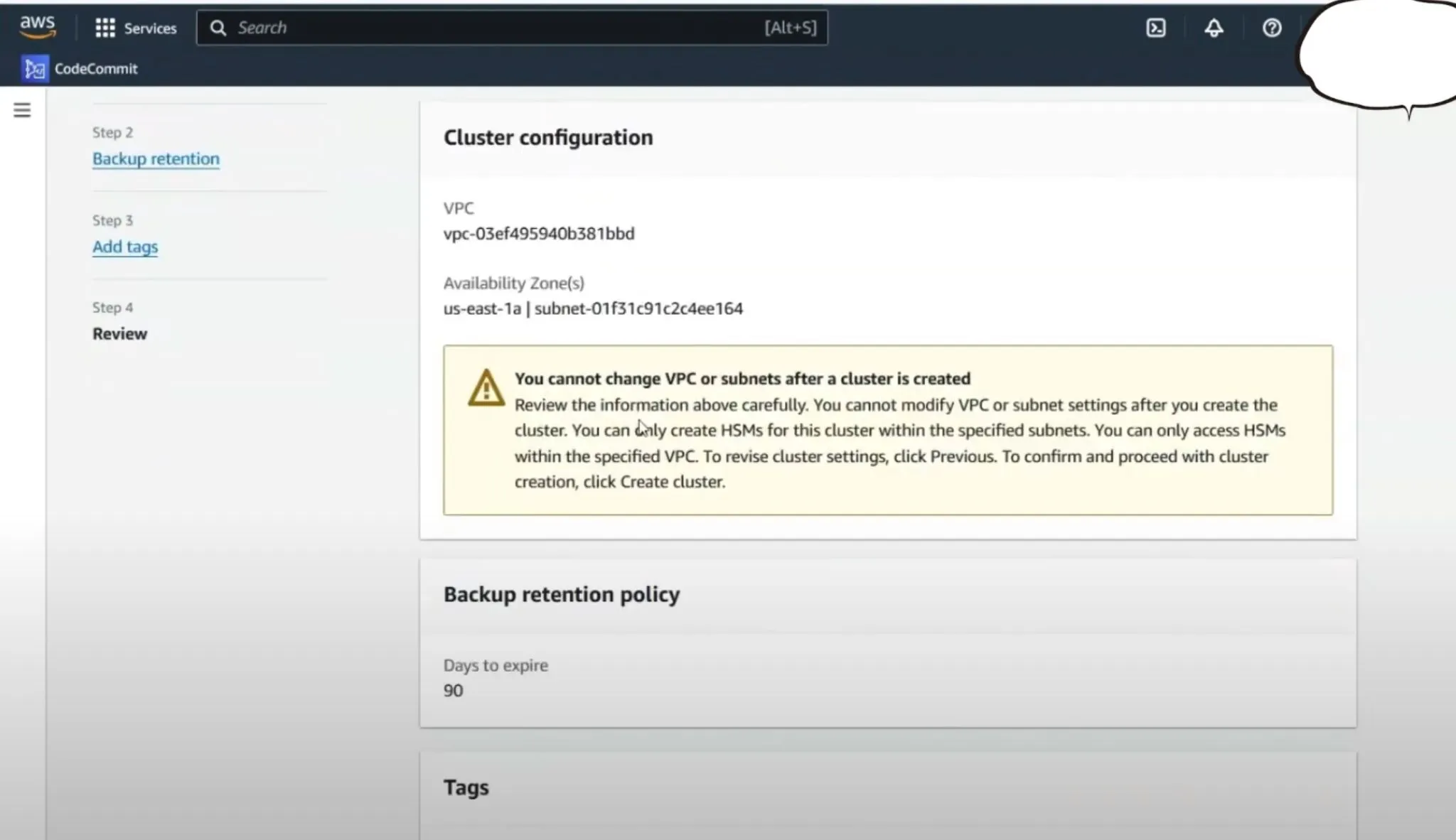
- Cluster Configuration: After providing necessary configurations like backups and tags, create the cluster. Once created, the cluster status will initially show as Uninitialized.
Initializing the CloudHSM Cluster
Key Management
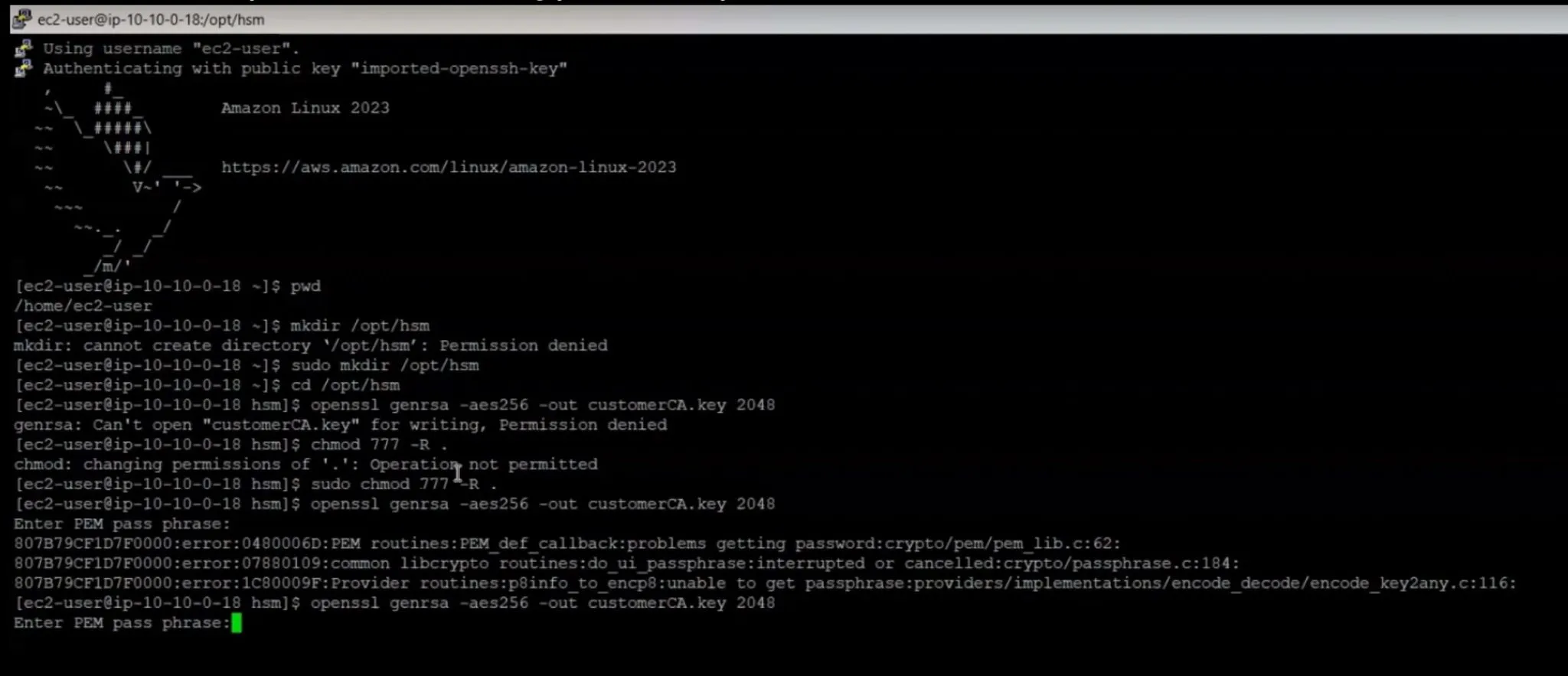
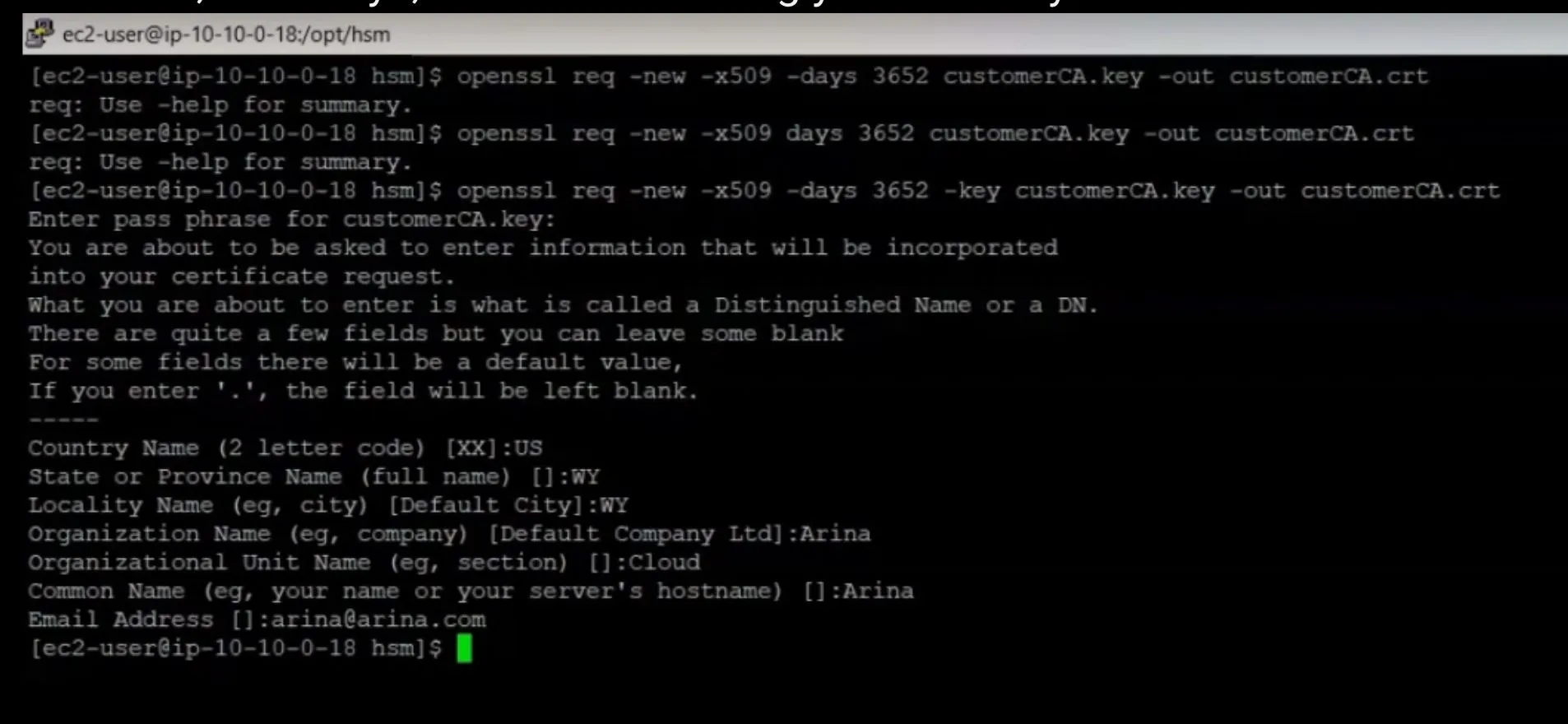
- Generate Key Pair: Before initializing, generate a new RSA key pair referred to as the customer key pair. This involves creating a private key and a corresponding self-signed certificate using OpenSSL commands.
Cluster Initialization
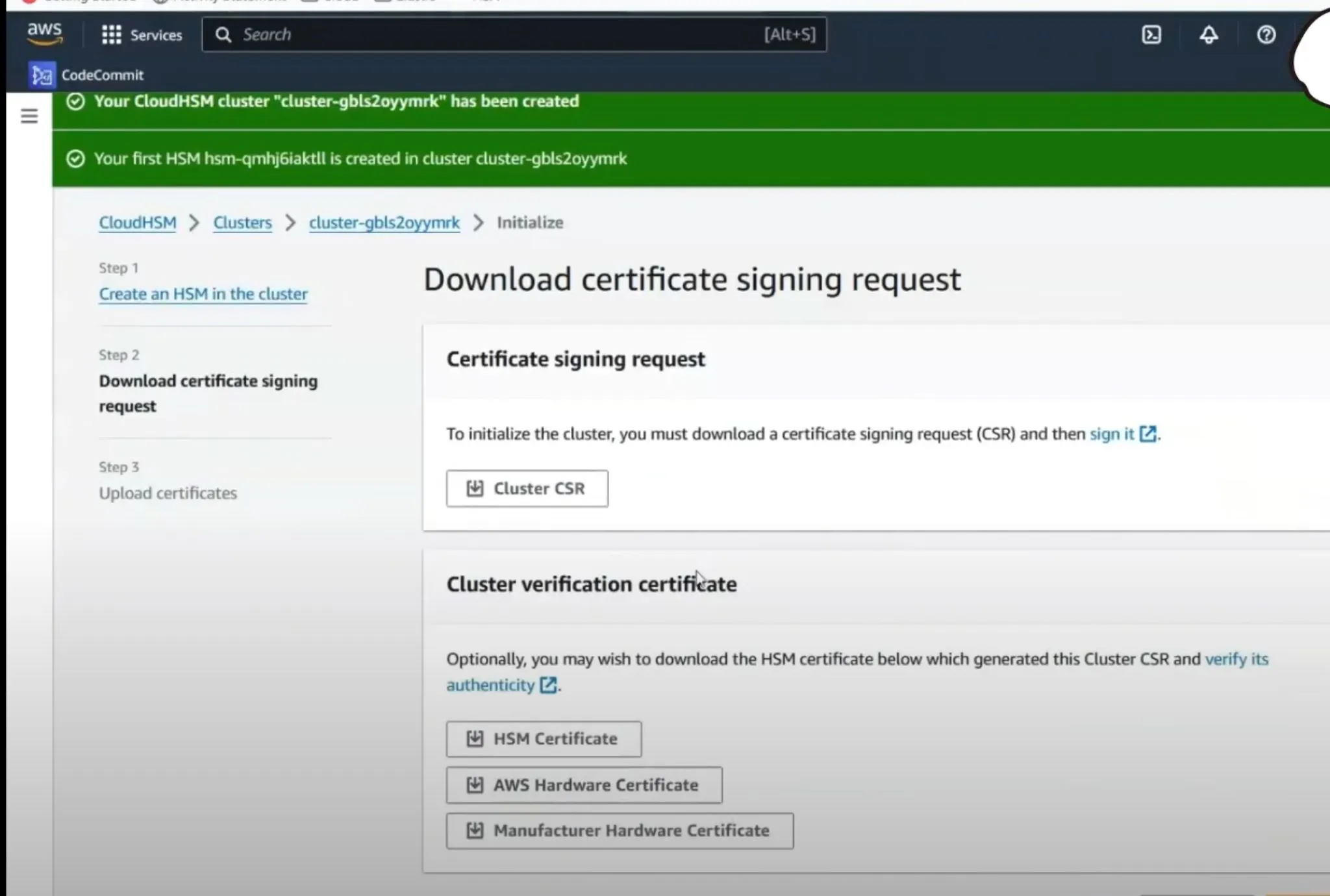
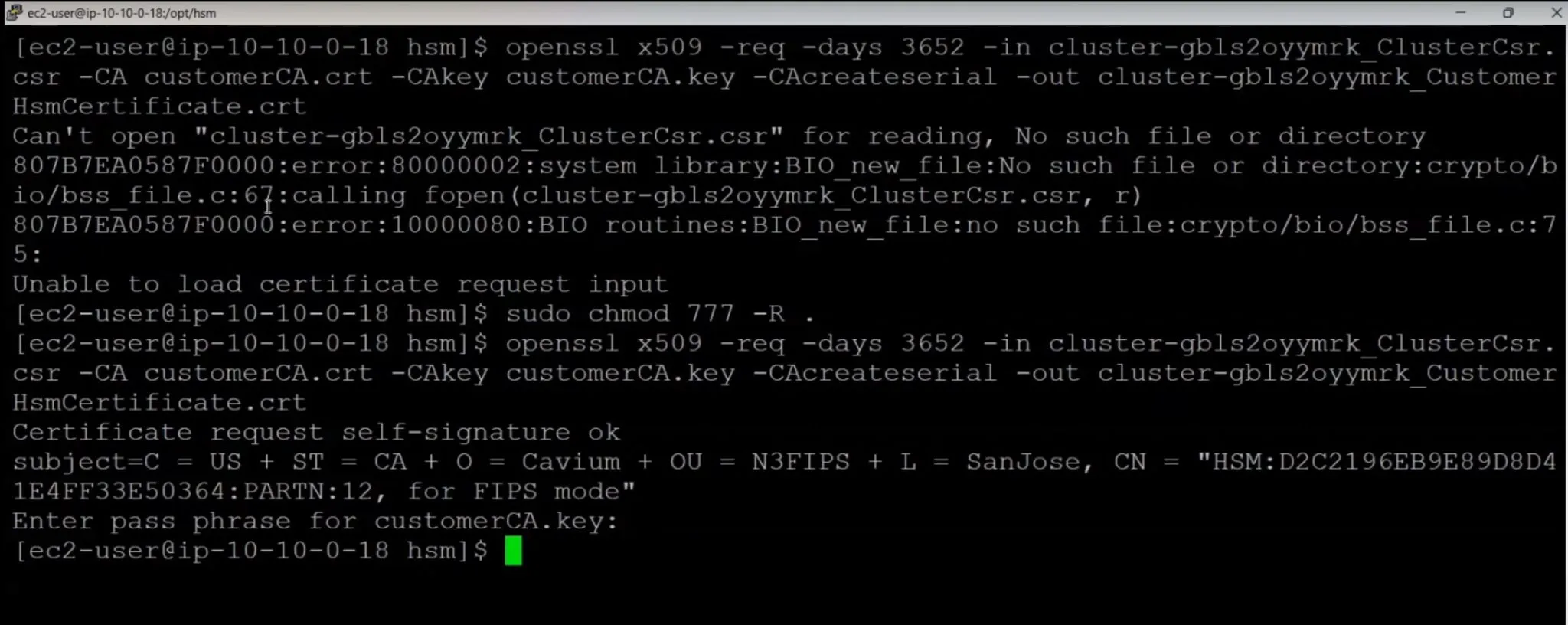
- CSR Process: Navigate to the 'Initialize' action in the CloudHSM console and create an HSM instance in your cluster. You will need to download a Certificate Signing Request (CSR).
- Sign CSR: Use the previously generated private key to sign the CSR. This confirms your ownership of the HSM cluster.
openssl x509 -req -days 3652 -in <Cluster_ID>_ClusterCsr.csr \
-CA customerCA.crt -CAkey customerCA.key -CAcreateserial \
-out <Cluster_ID>_CustomerHsmCertificate.crt
Upload Certificates
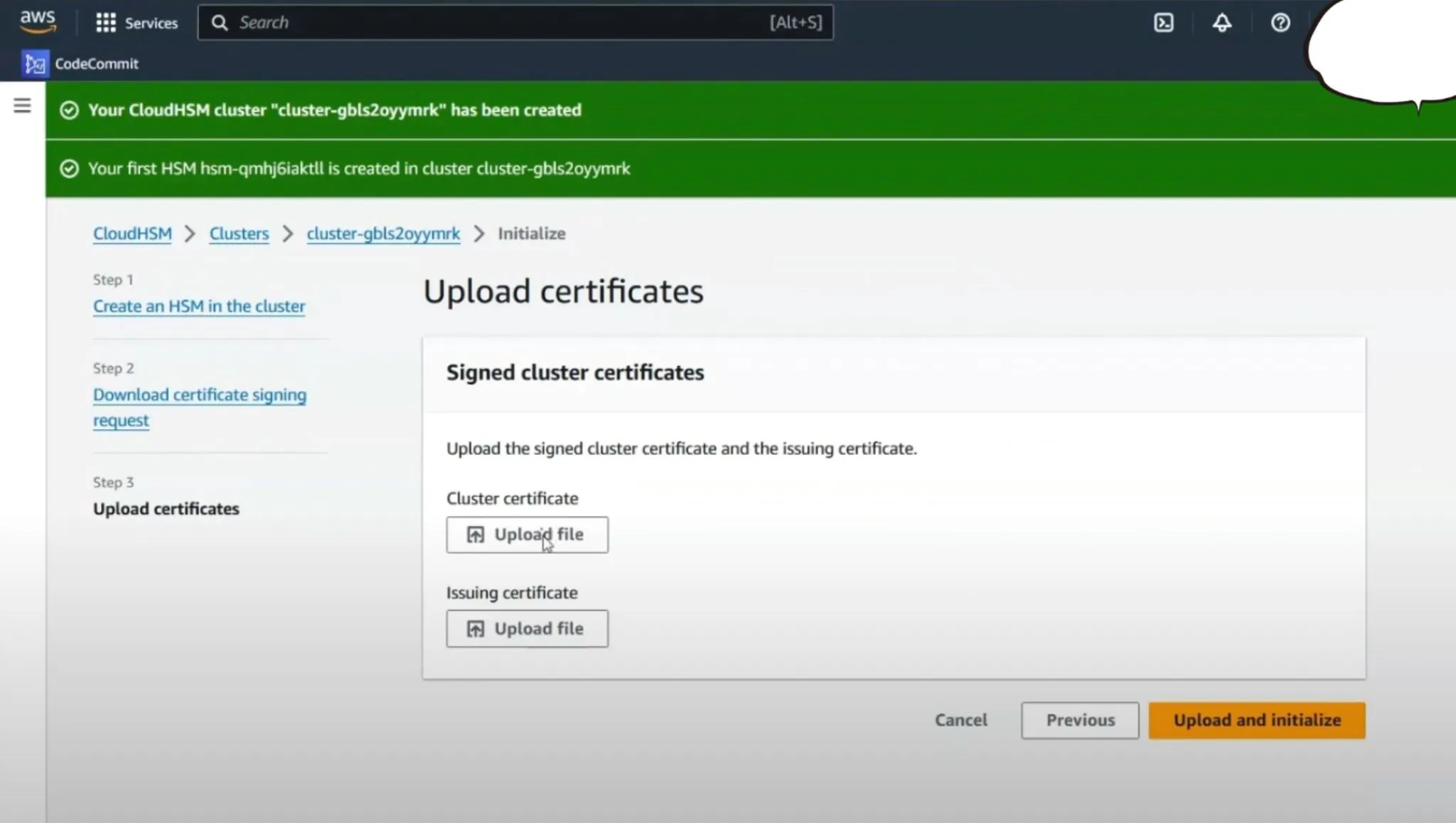
- Finalizing Initialization: Back in the AWS CloudHSM console, upload the signed cluster certificate and your issuing certificate. After uploading, finalize the initialization.
Activating the Cluster
Once initialized, configure the issuing certificate on each EC2 instance connecting to the cluster to enable the cluster's activation.
/opt/cloudhsm/bin/cloudhsm-cli interactive
cluster activate
Configuring HSM CLI and User Management
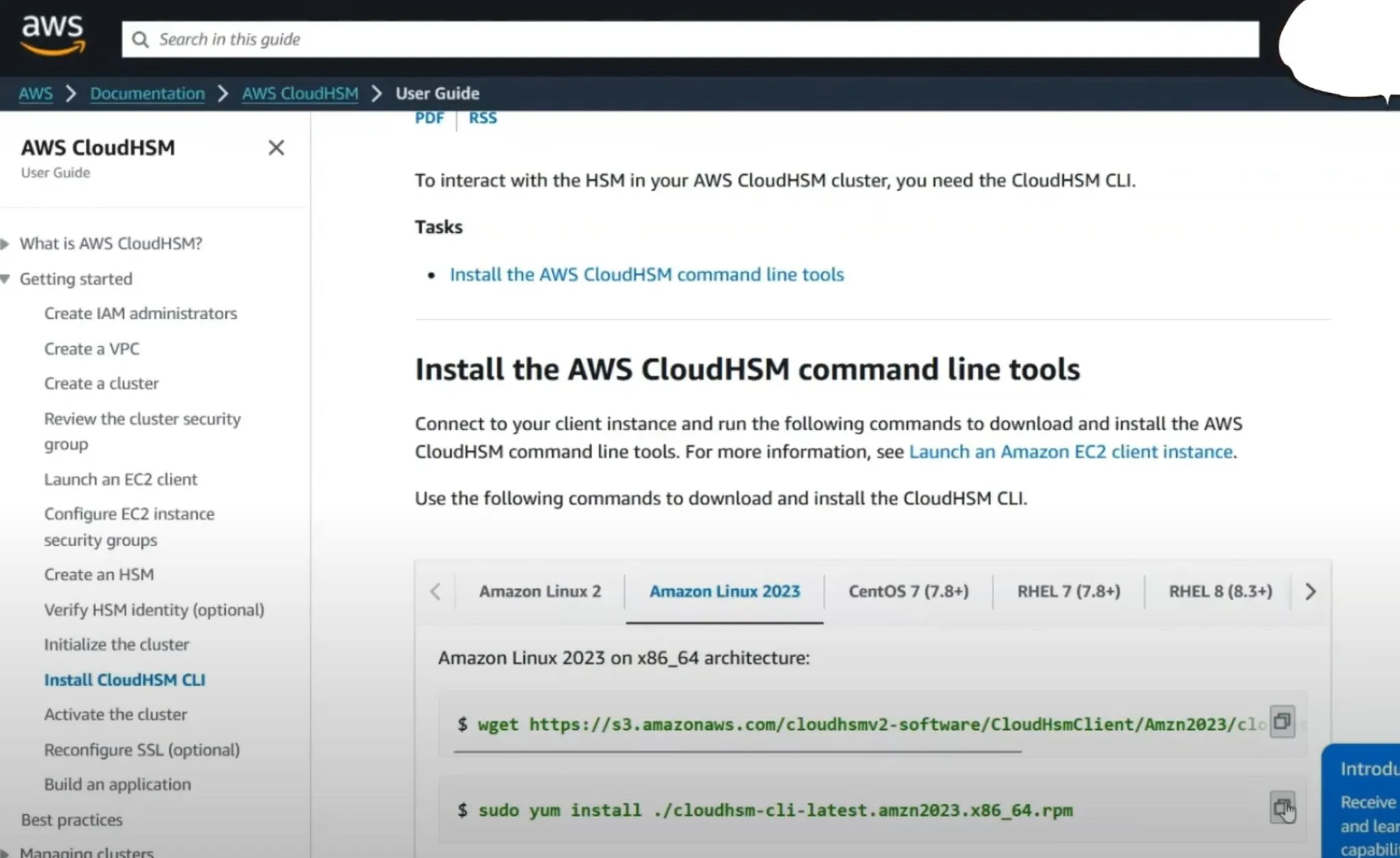
HSM CLI Setup
- Install CLI: Download and install the CloudHSM CLI tools on your EC2 instance.
wget https://s3.amazonaws.com/cloudhsmv2-software/CloudHsmClient/EL7/cloudhsm-cli-latest.el7.x86_64.rpm
sudo yum install ./cloudhsm-cli-latest.el7.x86_64.rpm
User Setup
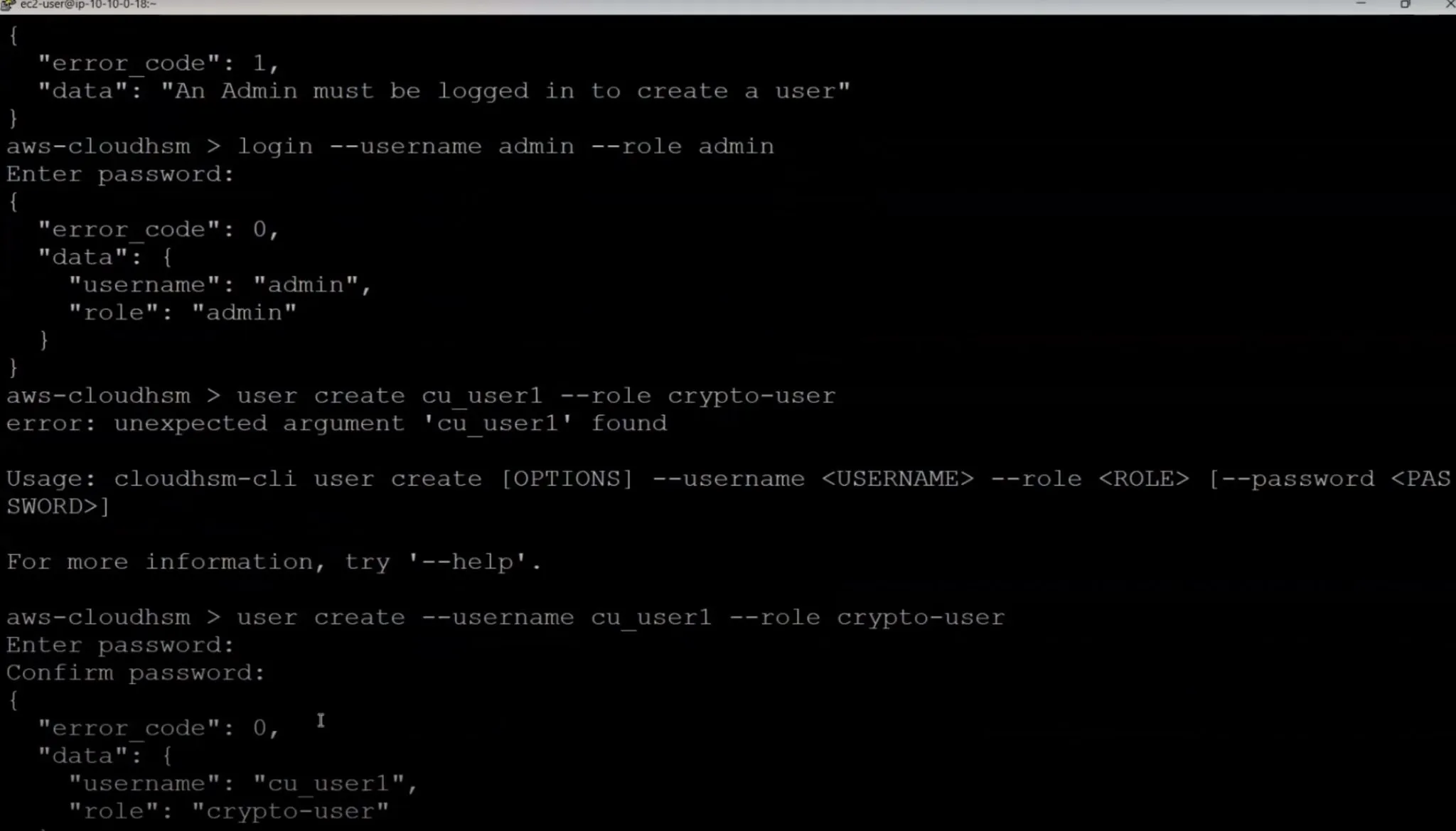
- Create Admin User: Utilize the HSM CLI to create an admin user. Once the admin user is set up, log in and start managing the HSM cluster.
user create --username admin --role admin
login --username admin --role admin
Crypto User Creation
- Manage Keys and Crypto Operations: Create crypto users (CUs) who will manage and use cryptographic keys. Each CU can create, delete, share, import, and export keys, and perform cryptographic operations like encryption and decryption.
Conclusion
AWS CloudHSM provides a secure platform for cryptographic operations in the cloud. By following these detailed steps, you can set up your CloudHSM cluster, manage keys and users, and ensure high security and compliance with organizational standards. This setup not only enhances security but also provides a scalable solution for managing cryptographic keys and operations efficiently.